How To Repair Crack In Pump Strainer Housing
If you lot've ever wondered how software pirates can take software and crevice information technology time and time once more, even with security in place, this small-scale series is for you. Even with today'southward about advanced methods of defeating piracy in place, it is yet relatively easy to scissure almost any program in the world. This is mainly due to computer processes' ability to be completely manipulated by an assembly debugger. Using this, you can completely featherbed the registration process by making it skip the awarding's key code verification procedure without using a valid central. This works because assembly allows you to speak directly to the processor and strength a skip over the registration process.
In this Null Byte, permit's get over how cracking could work in do by looking at an instance program (a program that serves no purpose other than for me to hack). I will not be walking yous through how to actually crack a legitimate plan, because I can't simply crack a program for demonstration, but the techniques applied to my examples should give you the foundation needed to create your own. At that point, it'southward a exam of your morals if y'all want to apply your knowledge for skillful or bad.
Requirements
- Windows (for examples merely, debuggers exist across platforms)
- A debugger installed: IDA, ollydbg, etc. (ollydbg volition be used in examples)
Step i Examination the Plan
Showtime, run the program that yous are attempting to reverse engineer and try to activate information technology with a random central to verify that you need a valid software key to go along. This is to verify that nosotros can come up with the keys.
Step 2 Run the Program in a Debugger
- Run ollydbg.
- Open up the plan you wish to bypass with ollydbg.
- Click the play button to run the program with the debugger attached.
- Right click the CPU window, and click Search For > All intermodular calls.
- Search for loftier interest DLLs. GETDLGITEMTEXT, will be for dialog boxes, which get called when you try to enter a software fundamental. By stepping into the function with the debugger, we can examine the registration specifically. SENDDLGITEM could exist used besides.
- Examination to see which one works to suspension out of the activation loop by right clicking the DLL telephone call and setting a breakpoint for all instances of that phone call.
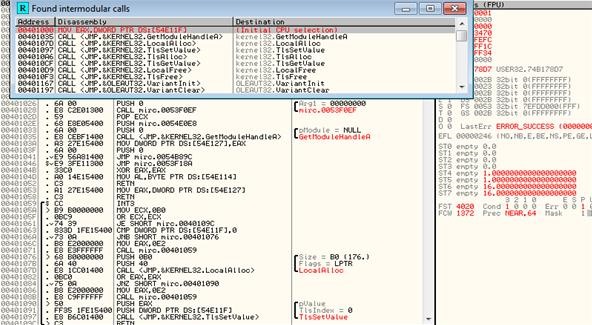
- Resume the program and enter any software central y'all feel like. If the debugger breaks (pauses the program'southward execution) after entering your key, then you know you found DLL in stride 5.
- Printing F8 back in the CPU window to force the adjacent step until you get to the Examination EAX. EAX is the render of a value, which ways that a cheque is being performed hither. Upon examination, we tin see that the EAX is checking for a number that is not equal to a aught value. This ways that if it is replaced with annihilation other than null, it volition run.
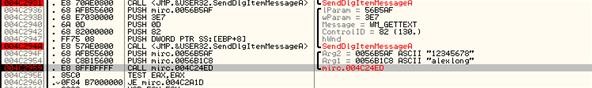
- Right-click the EAX and modify it in hex value to 1, instead of 0.
- Resume the program again, and you will accept successfully activated the program.
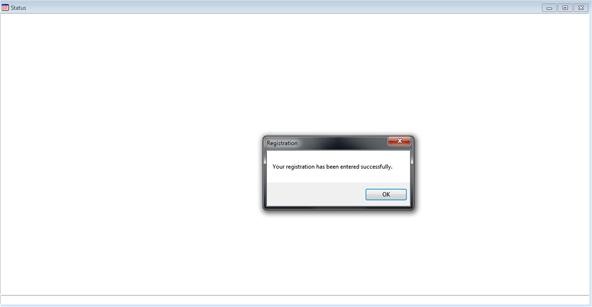 And for proof it was registered to me:
And for proof it was registered to me:
This works because you are making the procedure jump from one register and skip the one that verifies the fundamental entered. To exploit the central registration algorithm, keep an eye out for function ii of this tutorial on making the key generator. Hooray for associates!
- Post to the forums
- Chat on IRC
- Follow on Twitter
- Circle on Google+
Desire to start making money every bit a white hat hacker? Jump-start your hacking career with our 2022 Premium Upstanding Hacking Certification Training Parcel from the new Zip Byte Shop and become over 60 hours of grooming from cybersecurity professionals.
Buy At present (ninety% off) >
Other worthwhile deals to bank check out:
- 97% off The Ultimate 2022 White Lid Hacker Certification Bundle
- 99% off The 2022 All-in-Ane Data Scientist Mega Bundle
- 98% off The 2022 Premium Learn To Code Certification Bundle
- 62% off MindMaster Mind Mapping Software: Perpetual License
Source: https://null-byte.wonderhowto.com/how-to/hacks-behind-cracking-part-1-bypass-software-registration-0132568/
Posted by: grimesshichal69.blogspot.com


0 Response to "How To Repair Crack In Pump Strainer Housing"
Post a Comment